Introduction
Once upon a time there was an annual event put on by the Australian Government called CySCA. I was lucky enough to take part in this event in 2018 (the last year it has been run to date) and it was an excellent competition amongst the TAFEs and universities across Australia. The challenges were difficult and were a great learning opportunity.
Sadly it’s currently unknown whether or not CySCA will ever run again, but thankfully a coalition of university infosec clubs have banded together to put on an equivalent event.
Shoutouts
Naturally none of this is possible without people, and they deserve credit.
Organisers
A big thanks to the following groups for helping to put this on:
- Curtin Cyber Security Society (C-SEC)
- Deakin University Information Security Club (DISC)
- Macquarie University Cyber Security Society (MQ CyberSec)
- Monash University Cyber Security Club (MonSec)
- QUT Whitehats Society
- Royal Melbourne Institute of Technology Information Security Club (RISC)
- Swinburne Cyber Security Club (SCSC)
- Sydney Computing Society (SYNCS)
- TahSec
- University of Melbourne Information Security Club (MISC)
- UNSW Security Society (SecSoc)
- UQ Cyber Squad
- UTS Cyber Security Society (CSEC)
- UWA Ethical Hacking
It’s great to see a grassroots event establish itself in the midst of everything going on this year. Despite the adversity these uni clubs have made sure they have something that they can look forward to.
Teammates
- team:
I LIKE WHAT YOU GOT. GOOD JOB!- PlanetsOnly
- Markers
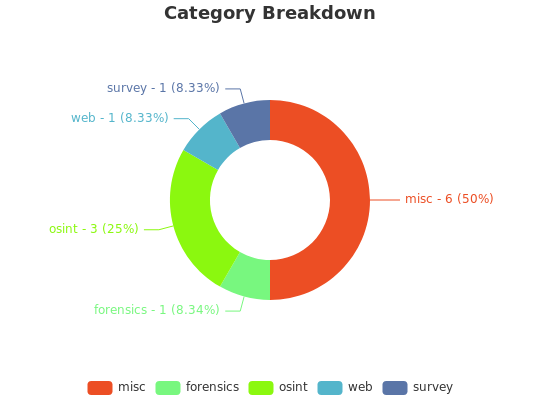
Categories
category | count | description |
|---|---|---|
| OSINT | 9 | Supreme google-fu skills required. |
| forensics | 6 | Plugging around inside data files trying to find stuff. |
| web | 7 | Web applications and techniques, browser business. |
| crypto | 9 | Number crunching and ciphers etc. |
| pwn | 7 | Buffer overflows and software short-circuting. |
| reversing | 4 | Decompiling, deconstructing and debugging. |
| misc | 13 | Everything that isn’t anything else. |
Challenges
Description
Check out our Twitter! Find the post with the flag! You can give us a follow if you like <3
Method
Go to twitter, find tweet.
RFVDVEZ7aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1YZlI5aVk1eTk0c30=
— DownUnderCTF (@DownUnderCTF) July 25, 2020
It’s base64, so we go to CyberChef for an easy conversion.
Heh, that’s a good flag.
Flag
On the spectrum
Description
My friend has been sending me lots of WAV files, I think he is trying to communicate with me, what is the message he sent?
Method
“Spectrum” is referenced by the title of this task, so my assumption is that it is a spectrogram-related task. Pretty low on the points scale too compared to other challenges, so I fire up Sonic Visualiser.
Definitely something going on down the low end of the frequency range, and after messing about a little with the spectrogram settings, I got a readable flag.
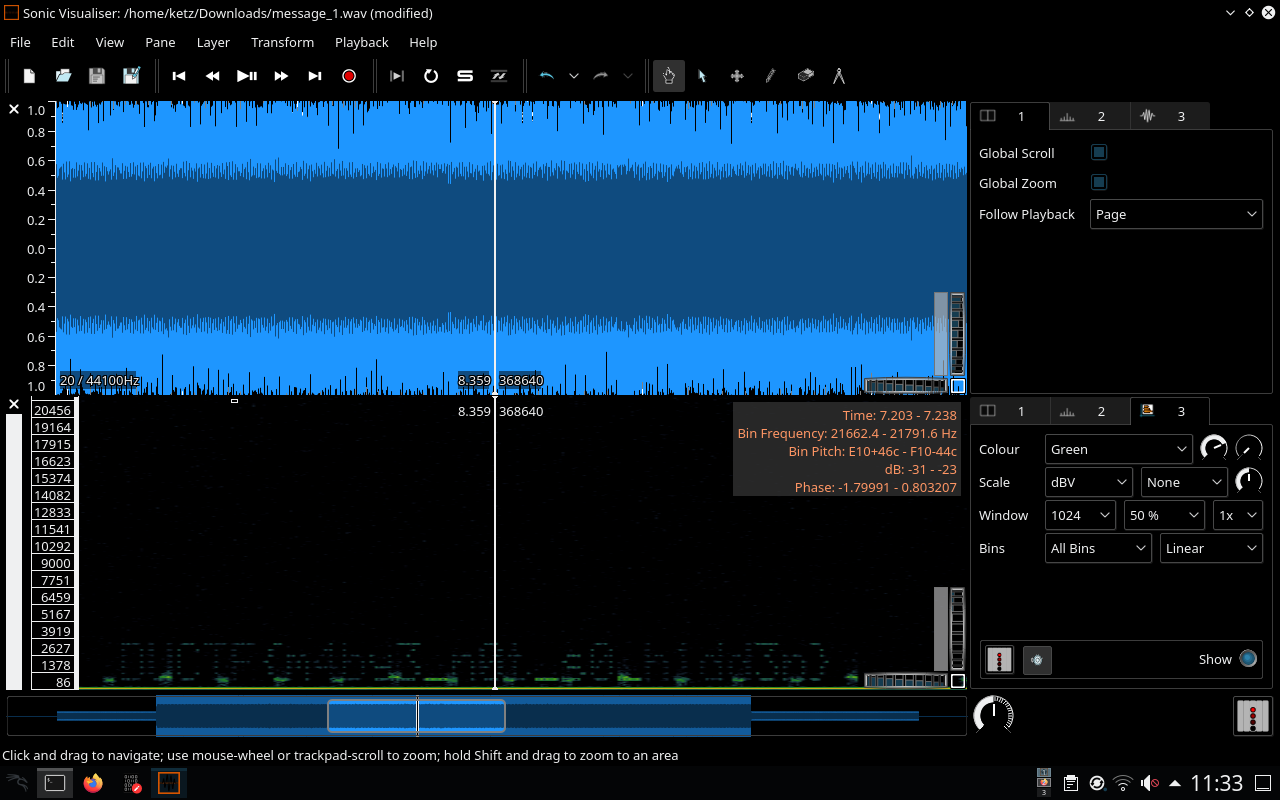
Flag
Bad man
Description
We have recently received reports about a hacker who goes by the alias
und3rm4t3r. He has been threatening innocent people for money and must be stopped. Help us find him and get us the flag.
Method
We’re talking about aliases here, so the first thing that’s worth a shot is checking out what services have the alias as a username in them. There’s a simple tool online called Instant Username Search which checks for valid usernames on different platforms (although the accuracy is questionable at best, it’s usually good enough). I found a bunch of accounts, but the meatiest was twitter.
Scanning over the tweets there is one that references accidentally posting personal information and being glad that there was a delete button. So this is a timeshifting challenge.
We go to the same page on the Wayback Machine and it looks like we luckily found the tweet that was deleted.
Flag
16 Home Runs
Description
How does this string relate to baseball in anyway? What even is baseball? And how does this relate to Cyber Security? ¯(ツ)/¯
RFVDVEZ7MTZfaDBtM19ydW41X20zNG41X3J1bm4xbjZfcDQ1N182NF9iNDUzNX0=
Method
Moar base64, what a wonderful time!
Use CyberChef to decode it and we’ve already hit the flag. Nice!
Flag
In a pickle
Description
We managed to intercept communication between
und3rm4t3rand his hacker friends. However it is obfuscated using something. We just can’t figure out what it is. Maybe you can help us find the flag?Files
data
Method
I have heard of Python pickling before, it’s a Python way of object serialization / deserialization. I’ve never done it before so I did a quick google and it’s a fairly straight forward process (at least in this case).
I started off by writing this script:
import pickle
data = open("data", "rb")
out = pickle.load(data)
print(out)
Which gives us:
{1: 'D', 2: 'UCTF', 3: '{', 4: 112, 5: 49, 6: 99, 7: 107, 8: 108, 9: 51, 10: 95, 11: 121, 12: 48, 13: 117, 14: 82, 15: 95, 16: 109, 17: 51, 18: 53, 19: 53, 20: 52, 21: 103, 22: 51, 23: '}', 24: "I know that the intelligence agency's are onto me so now i'm using ways to evade them: I am just glad that you know how to use pickle. Anyway the flag is "}
Reading between the lines we’re about halfway there. We still need to convert some of the items in the pickle because they are decimal representations of ASCII characters and need to be converted to ASCII.
So let’s change the approach a little bit. We can easily read the “plaintext”
of this elaborate encryption strategy, so we’ll just ignore that for now. What
we really want to get is the actual contents of the flag. We need to convert
the decimal values to characters, and we can do this using Python’s builtin
function: chr().
import pickle
data = open("data", "rb")
out = pickle.load(data)
decimals = range(4, 23)
for i in decimals:
print(chr(out[i]), end="")
Now we get
p1ckl3_y0uR_m3554g3
This looks like the meat that we’re looking for in our flaggy sandwich, and it
turns out it is. We just need to wrap it in two slices of DUCTF{ and }, and
we’re golden, nice!
Flag
Pretty Good Pitfall
Description
PGP/GPG/GnuPG/OpenPGP is great! I reckon you can’t find the message, because it looks scrambled!
Files
flag.txt.gpg
Method
This challenge is actually a good cautionary tale for folk who are new to GPG. It makes a point of the fact that merely using GPG on a file and making the insides of it scrambled does not make it encrypted.
Why is this? Well, it’s possible to use GPG keys to merely sign something,
meaning that it can easily be returned back to its plaintext state. Getting the
flag.txt out of this flag.txt.gpg is as simple as running:
$ gpg flag.txt.gpg
GPG then digests the signed file back to its original format and we get our
flag as a new file: flag.txt. A good lesson of something that can easily go
wrong when using GPG if you haven’t had much practice with it.
Flag
Leggos
Description
I <3 Pasta! I won’t tell you what my special secret sauce is though!
Method
How do you view source when the web page won’t let you? Hmmm, tricky indeed. There are a few approaches you could take for this challenge. It was pretty clear from all the hints about sauce that we needed to view source.
The webpage that we were greated with prevented the common keystrokes to open
up devtools or to view source for the page. To get around this I added
view-source: in front of the URL and tried again.
I couldn’t see the flag in the page contents, but a visit to the javascript file that was blocking the keystrokes, was enough to get that delicious flag.
Flag
Off the Rails 2: Electric Boogaloo: Far from Home
Description
Okay so I’m starting to think I may have got on the wrong train again and now it’s snowing so hard I have no clue where I am 😬. Thankfully, I managed to snap this pic before the storm started. We seem to have stopped at this station.. can you tell me it’s name?
Please tell me the name of the station in lower case flag format, with any spaces replaced by underscores.
Files
no_pain_no_train.png
Method
So basically, we have a picture of a place in the world, and we need to figure out where it is.

This isn’t really heaps to go on, but luckily I have some experience in trains.
The most iconic thing about this image is the Red building near the railway. In Norway, many of the houses and railway buildings are distinctively coloured red in this way. So I already knew it would be somewhere in Norway.
I spent a bit of time casually looking through every single train service in Norway but this was not very effective, so I changed up the process a bit.
Knowing that it was in Norway, I determined via process of elimination (essentially bruteforce) that the model of the train in the picture was a NSB Di 4, owing to a combination of: the positioning of the lights, the window shape, red colouring and distinctive yellow snowplow.
The Wikipedia page for this particular class of locomotive says that it only serves a single line, the Nordland Line. So we now have a pretty narrow field left to search in, getting closer.
Another great thing that Norway does, is the so-called Slow TV programs that they create, very often being journeys via some form of transportation. These programs were originally started out on the trains, and thankfully this practice has spread far and wide across Norway, so we could find a video of the Nordland line and review each station.
I found the above video, and someone had kindly created a list of timestamps for each station which sped up my search immensely, I clicked through each one until I arrived at Dunderland. In fact, if you got to exactly 7:19:40 in that video, you get almost exactly the same image as the one from the file.
We found the station! Awesome!
Flag
Outback Stakeout
Description
My favourite place to grab a snack. Where is this and, how many dishes are there?
Please let me know in flag format with the location in lowercase and underscores instead of spaces, followed by the number of dishes:
DUCTF{location_dishcount}Files
dont_dish_out_what_you_cant_take.jpg
Method
We’re given the following image.

Straight away I knew exactly what this was. But for the sake of a writeup, let’s think a bit about the context of this CTF event.
This is DownUnderCTF, celebrating everything about Australia, whilst also being completely about infosec. This is an image of Pine Gap, a US surveillance station that’s situated in the Northern Territory, not far from Alice Springs.
Flag
Summary
It’s been a massive week for me, I started working in a new place and had to get up to speed with heaps of new things for that so I wasn’t feeling super competitive for this event when Friday came around. Having said that, I think I put a pretty decent effort into it without burning too many precious weekend hours in front of a laptop.
This event had a great mix of challenges both in terms of category and difficulty, and I think it’s done a great job of replacing the idea of CySCA. I think it actually became a bigger event than CySCA with a higher difficulty curve towards the top end.
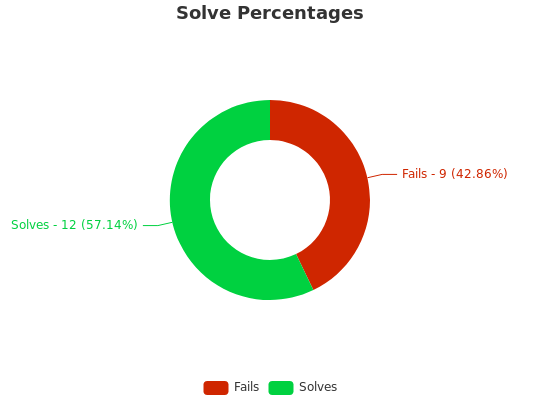
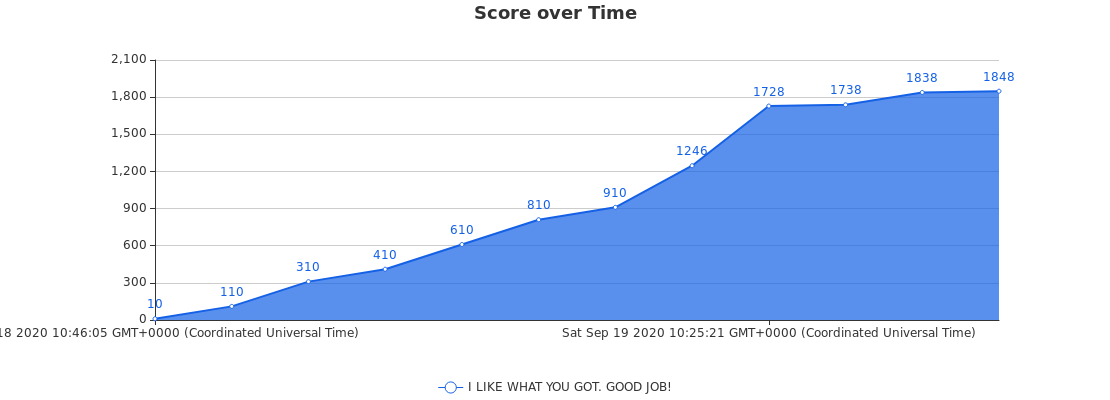
The results are up on CTFtime, we ended up in
171st place with 1848 points, which is a pretty pleasing result from an
event that I personally didn’t put too much effort into. I didn’t really
learn much in the way of new stuff this time around because I stuck to the
things I was familiar with. Perhaps next time I’ll look into weird and wacky
business and actually try to learn a new skill or two.
Thanks a lot to the organiser’s for a great job, it’d be really cool to see this become an annual event, but that’s still something to be seen in the future.
That’s all for now, looking forwards to the next one 😃
Graphs